Ransomware is costing commercial business billions of pounds worldwide every year. In the United States alone, from those that report paying the ransoms, totals are expected to hit £763,000,000 (US$1.06 billion) this year. Those that seek out other solutions to get their information back still have the cost of their data being inaccessible for days; and that’s not to mention those that are completely wiped out because they couldn’t afford to pay the fees demanded. The cost is skyrocketing. These cybercriminals are not meeting enough resistance to dissuade them from attempting to blackmail small businesses everywhere.
Back in January of this year, you may have heard about how Lincolnshire County Council was obliged to shut down their entire computer network when it was breached due to a staff member opening the wrong e-mail attachment. The £1,000,000 ransom demand went unpaid, of course. The council sought another solution, like many others do, working with security experts to decrypt and restore some files, and recovering many others via their backup system.
Unsurprisingly, hospitals absorb about 40% of all assaults worldwide because lives hang in the balance and they are among those more likely to pay. Facing missing surgical directives, treatment regimens, and drug histories can mean bringing everything to a halt, risking innumerable lives.
How not to respond
Just about every security expert will tell you “Don’t Pay!” However, in a move which stunned nearly everyone, a member of the FBI in the United States rather candidly admitted that if a victim needs their data, that they should pay the ransom.
“The ransomware is that good,” said Joseph Bonavolonta, the Assistant Special Agent in Charge of the FBI’s CYBER and Counterintelligence Program in its Boston office in 2015. “To be honest, we often advise people just to pay the ransom.”
What the FBI says carries a lot of weight, making a difference to and influencing the decisions of many people. Security experts are saying this is the most irresponsible position they could have taken.
Consensus among experts in the IT industry is that paying the criminals is absolutely no guarantee that you will ever be given the decryption key; that they’re just as likely to take your money and disappear, with no regard for your data; that paying them is simply rewarding criminal behaviour.
A prime example of ransomware that does not unencrypt your computer, even when the criminals are paid off, is the “Police-themed” ransomware. Its effectiveness is predicated on the embarrassment or fear caused by official-looking communications, which state that “This computer has been locked because it is violation of the laws of [insert Country] we have detected…” and then lists Pornography, Violence, Child Pornography, Zoophilia, and Spam messages with terrorist motives. It demands a fine (approximately 100 Euros) to unlock the computer. Fortunately, it’s very easy to remove with free online tools.
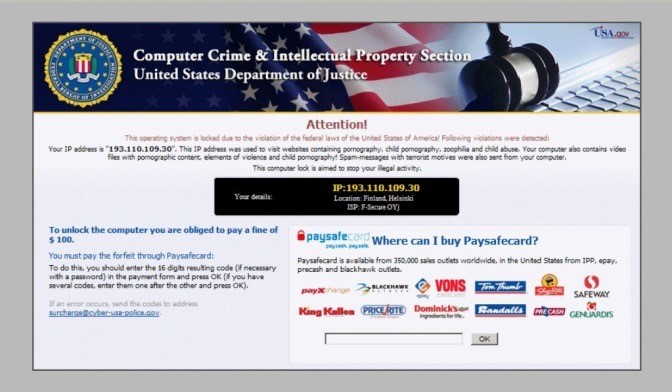
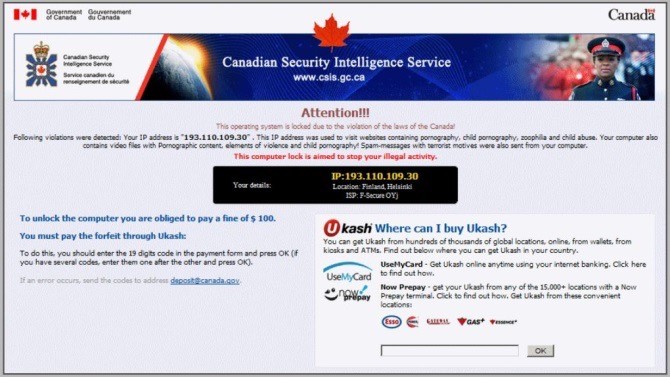
If, however, you are reasonably cautious, you should be able to protect yourself, and never give these criminals anything. Those that don’t heed good advice may end up paying for their mistake.
How to Protect Yourself
Stay Up-to-date
Be diligent about installing patches and updates for your applications. Software producers don’t put them out because they’re fun to make. They often do provide increased functionality, but more importantly, their best and most practical purpose is to patch security vulnerabilities.
Trust No One
Fox Mulder probably “had it right” for somewhat different reasons. If you receive peculiar, unusual, or unexpected e-mail, especially with attachments, speak to the sender and ask if they actually sent it before you open it. It’s fine to open the e-mail—you cannot get infected that way. But if there is an attachment, you definitely should not open that. Nor should you click on a link in an e-mail, even if it has no attachment. “Safe-looking Hyperlinks” are just as dangerous because of where they can take you. Hover over it to see its (potentially non-existent) destination.
Back Up Your Files Regularly
For a small business, there are long stretches where your computer system is essentially dormant. Use that time to create a system image. Large external USB hard drives are remarkably inexpensive nowadays. Make a weekly System Image — or even daily if you prefer — which is an exact copy of all of your stored files. 3:00 AM is a fine time to make backups.
Do it once a day and you’ll never lose more than a day’s worth of data. If everything were to be encrypted, you could format all of your storage and copy the last backup right into place to completely remove the offending application.
Just make sure you disconnect the backup system whenever you’re not using it so that it is safe in the event of a ransomware attack.
Malware evolves
What is true today may not be true tomorrow. Currently you should be aware that not all files are targets. Ransomware generally focuses on data-related materials such as images, documents, and spreadsheets. The bulk of your system remains essentially untouched.
You can utilise your operating system to perform daily backups of all new documents, spreadsheets, images and any data-related files in record time, and store them on thumb drives, DVDs, or anything that doesn’t remain connected to your main computer system. You might simply delete the affected files, and restore fresh copies after the malware has been removed.
The Cloud makes it Easier
Your data is not immune on a Cloud server. It can be infected just like any other server. However, if your storage resides on The Cloud it is almost a non-issue, provided you selected a good service; they make sure that everything is backed up regularly.
Despite the fact that you’re sharing space with innumerable other servers on the same rack, the virus cannot propagate from a different server onto your server, or vice versa. Your server and backup copy are both safe and discrete, and in fact may exist in multiple locations around the world so that a customer in Singapore or Brisbane doesn’t need to contend with the intrinsic delays of using a London-based server.
Your provider’s backup copy may be almost continuous, meaning it might be only a few hours old, or with high security firms, perhaps only minutes old. That largely depends on how much you are willing to pay for the provisioning of your services.
Train your employees
Given a well-to-do organization as a target, the amount demanded could be stratospheric. Savvy businesses and institutions are better protected than most, but the high-level crooks choose targets with plenty of employees, knowing that statistically, 20% will open any e-mail, and perhaps one person (the only one necessary) might click the link.
If only 0.5% of 200 recipients were blithely ignorant enough to click such a link or open an attachment, the odds are in the criminal’s favour that they will be able to invade your system. That is why security companies are prepared to teach your employees how to recognize malware.
Such companies generally utilize a two-pronged training methodology which can be experienced in either order. One step involves sending simulated phishing attacks to all your employees. The others step involves a series of short videos which can be experienced as time permits.
Beginning with the simulated phishing attacks can create awareness that a problem exists, and thus create enthusiasm and engagement for the subsequent video portion. Starting with the video program could provide an immediate awareness. Following up with the pseudo-phishing attacks could keep awareness levels fairly high. You will have to make a judgment call based on the tenor or disposition of your staff members.
Prevention is the Key
Not to promote any particular company, but Malwarebytes has a decent history of fighting malware. They have now introduced a new product called Malwarebytes Anti-Exploit which comes with a 14-day Free Trial. Their introductory video is quite enlightening. There is no connection here other than relevance of the material (which is informative, albeit essentially a commercial). It has an annual fee, if you decide to keep it, and it does look promising.
Show File Extensions
For some incomprehensible reason, software developer and engineers came to the conclusion that users didn’t need to see the file extensions. Users were apparently deemed too ill-educated to understand them, and so they were hidden. Something could be called DocumentYouWanted but actually be DocumentYouWanted.exe and many would be none the wiser. “Oh, it’s the document I wanted. I’ll just open it…” whereupon all hell would break loose. It is, however, easy to fix.
For Windows OS: Click START; type “folder options” in the search box (no quotation marks) and open it when it appears at the top of the list; click the VIEW tab at the top and clear the checkmark from the Hide extensions for known file types-ON so that it reads Hide extensions for known file types-OFF. Click OK. You’re done.
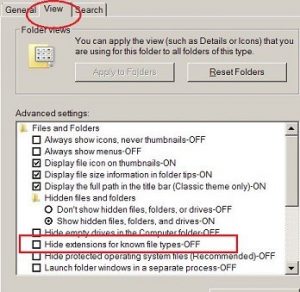
For Mac iOS: Open a new Finder window on your Mac; open Finder, then sub-menu Preferences…; Click on the Advanced tab, and make sure there is a check mark in the first box which is labelled Show all filename extensions. See how simple it was?
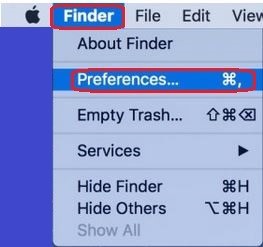
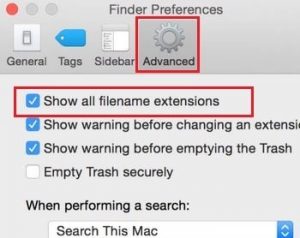
And that’s a large part of what it takes for you to be safe. Now you can see when the file is an executable file, when it’s a PDF file, and when it’s a document. You are now in a position to make sensible decisions, despite how little faith the designers may have in their users. Prove them wrong! Show them that we are capable of recognising and interpreting the file extensions, and differentiating between an innocuous and dangerous file.
Use powerful, reliable antivirus software
At the very least use a free alternative such as Avast™, or AVG™ to offer fundamental protection. You should be aware that if you have upgraded to Windows 10, that Microsoft™ is well-aware that Windows Defender (the built-in AV programme) is not the best tool available. It is the default tool because everyone needs something—and it will automatically disable itself if you install something better—but if you disable it without a replacement, it will turn itself back on in very short order.
Irrespective of what you choose to use, make sure that the heuristics function is turned on. Heuristics allows the antivirus to run the programme in a virtual environment and analyse what it does before it allows it to run on the machine proper.
If it attempts to overwrite file names, hide itself, or replicate itself, the user can be alerted to this virus-like activity. An alternative method includes decompiling the program to look at its code. If that resembles known virus code or utilises common virus functions, it is also brought to the user’s attention. New viruses and malware can be discovered by their behaviour, even if they are brand new and unknown (often referred to as zero-day viruses).
What do I do if I’m already infected?
First of all, disconnect from your Wi-Fi and Network so it cannot spread further. Via a separate uninfected computer, or device, connect to Europol’s No More Ransom site, or alternatively, the decryption site operated by Kaspersky (the antivirus anti-malware people), which is cooperating with Europol. They have decryption tools for several of these ransomware suites. You can copy an encrypted file from your machine and upload it so they can help you identify which cryptographical programme was used, whereupon you may be able to decrypt your computer without paying the ransom and lining those criminals’ pockets.
Ultimately, that is the best choice. If you don’t have backups to restore your material, do everything in your power to avoid paying these reprehensible thieves. Our ability to decrypt ransomware attacks is improving every day. The less money we allow them to extort, the quicker this nasty little novelty will dry up and they’ll go on to some easier way to steal from people.
Something to think about
If I lost all access to my company information right now, what could I do about it? Am I, in any way, prepared to deal with it?
You shouldn’t blame your IT people if they don’t have the funding, oversight, or direction to protect your business. Consult with them now and get this sorted out before it becomes a real difficulty.
The Takeaway
Make sure you are using the most modern versions of any software you possess. Old versions may be comfortable and familiar, but new versions offer the best protection for you and your data.
When three out of every four businesses have been the victim of malware, this is no longer something that “we should consider some time in the near future”. It is vital that you take steps to understand just how vulnerable you are and do something about it today.
There is no institution, business, or individual that cannot be a target. Failing to take reasonable precautions is in your hands, and it could cost your business dearly.